#7 Securing the Teleworker
Subscribe to get the latest
on Mon Jul 13 2020 17:00:00 GMT-0700 (Pacific Daylight Time)
with Darren W Pulsipher, Steve Orrin,
With the huge shift in people now working from home instead of the office, security is a growing concern for many IT organizations. In this episode, Steve Orrin, CTO of Intel Federal, and Darren discuss the security threats and solutions to help secure your teleworker and enterprise data centers.
Keywords
Listen Here
Teleworker Modes of Operation<h2>
The teleworker modes of operation are not new, whether it is using a device as a terminal (VDI), part of the internal network, or as a portal to services/software (SAAS); what is new is the sheer volume of employees, contractors, and partners all now using existing environments to do their core work, rather than a select, manageable few. Security is a challenge in all of these modes of operation. Organizations need to figure out how best to deploy their existing capabilities to secure and protect access, data, devices, and users.
Threats of Teleworking<h2>
Some of the security threats are those that have always been present with teleworking: security of the end device and data, the access point, and access to enterprise services. In adapting to the COVID-19 environment, however, new problems have arisen because of the large number of people now teleworking and the mad rush to enable them.
One issue is workers at home in unsecured environments on networks that were never intended to be used outside of the corporation. This leads to targeted phishing and malware attacks. Another problem is the introduction of new tools, such as those for collaboration and video conferencing that can expose your enterprise and data to attack and malicious use. Basically, there is now an increased attack surface area, much larger than what most organizations initially planned for, and new environments that were never part of the original plan.
Solutions for Securing the Teleworker<h2>
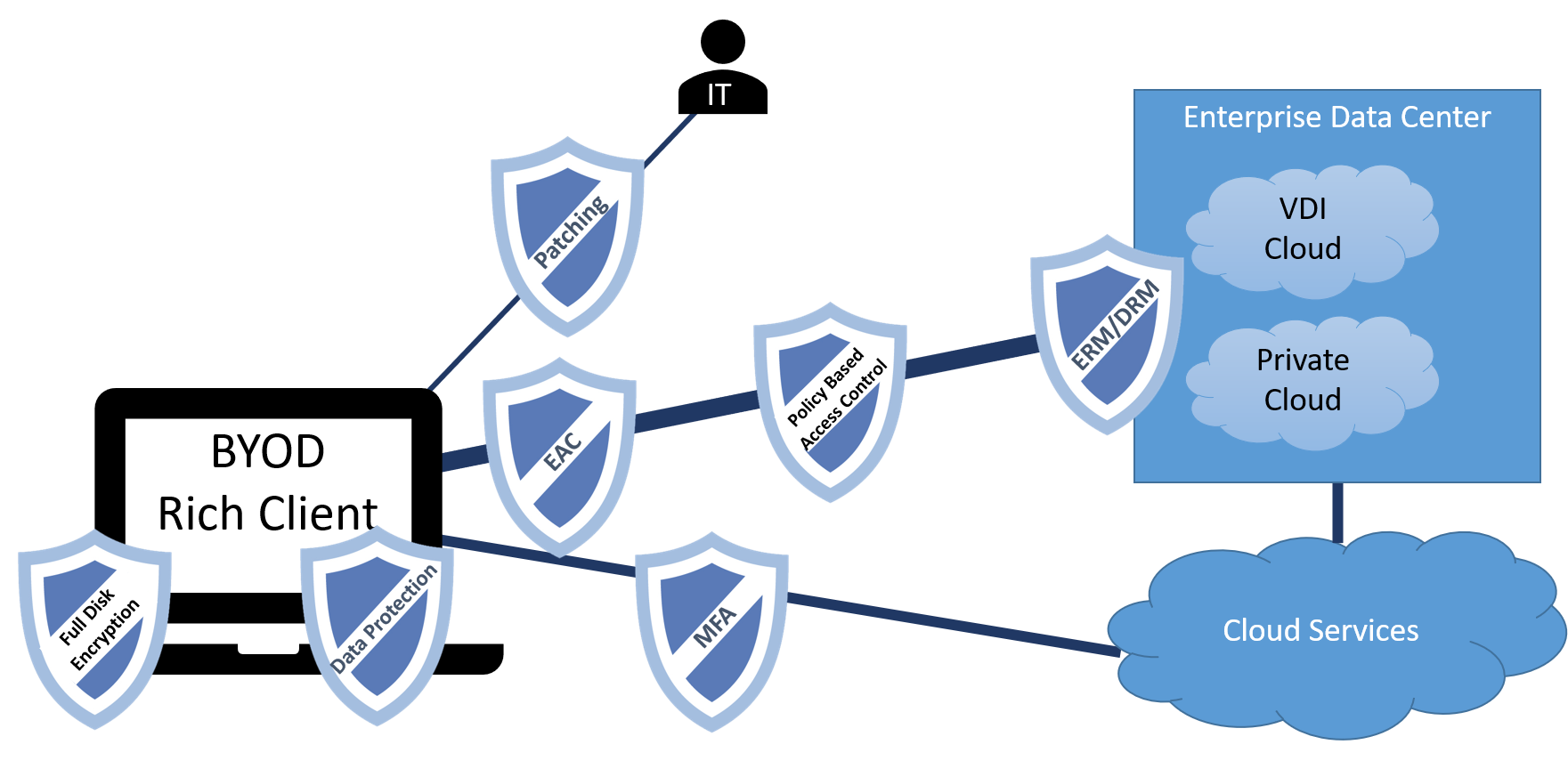
Bring your own Device (BYOD)<h3>
One of the harder issues to deal with is when workers use their own devices. The key challenge is that these are unmanaged devices without all the security agents running and managed by IT; the device is owned and managed by the user. You may have the ability to load a few agents or have some enforcement of policy, but there’s only so much you can do without impeding the worker utilizing it as a personal device. So how can you secure a user with a BYOD?
Make sure these basics are in place: Push the latest patches as a requirement, enforce good access control to your enterprise and services, implement multi-factor authentication, and surround your assets with the right protections such as enterprise rights management for access control of the data and enforce end-point, policy-based access control.
Another option to reduce your risk may be to limit direct access to enterprise services and have users work in a SASS environment.
End Points and Unsecure Environments<h3>
The best solution for many of these problems would be an enterprise rich client, but there is still risk involved. Workers are using a device that is a managed extension of the enterprise network. Security can be in place with a secure boot, full disk encryption, data protection, local firewalls, and enforcing good patching. The risk, however, comes because many organizations already have remote workers in place, such as sales people or field engineers, who may not have the same level of security as workers who were never meant to leave the building, such as finance and human resources.
Organizations must be vigilant about making sure all workers now have the same security, or even adding extra layers that workers need to work remotely in unsecured networks. Multi-factor authentication should now be a requirement, and end point policy enforcement and enterprise rights management are now more important than ever.
We are seeing innovations in this area, such as one customer who is giving new employees not just laptops, but also a managed router to avoid unsecured networks.
VDI Systems & Cloud Services<h3>
Implementing security for both VDI systems and cloud services includes the security basics: data protections, virtualization security for both the enterprise data center and at the access points, application security, secure boots, patching, and network encryption. The key is doing an accurate survey of the enterprise and cloud services that are being deployed to your workers and making sure that they are all secured equally. Each application, even those that are not mission critical, is a potential attack point.
As-a Service Clients<h3>
SASS clients use services in the cloud and also use applications on their rich client, so there are some additional security issues to worry about. There should be appropriate data protection in enterprise rights management (ERM) for the access to the data through the cloud services and back to the data center. Protection at both sides is critical. Client access to cloud services should be protected through multi-factor authentication and network encryption. The cloud service access to the enterprise data center’s private cloud and enterprise resources should also be protected at the network and data access and application layers. Understanding how clients are using the services and what data they are accessing is where the ERM decisions come into play.
Misuse and Abuse Insiders<h3>
IT should use a variety of methods to manage the threat and risk of mistakes, misuse, and malicious actions of insiders. Policy-based access control and enforcement from applications to data at both the enterprise and the cloud level is important to thwart misuse and abuse of users who are already authenticated. The major defense that IT has is auditing and monitoring threat intelligence. Managing this information across the enterprise and the cloud over a long period of time can be very effective in detecting aberrant behavior.
There is no question that we have to think differently now about security issues with teleworking. Our top recommendations are first, deploy the technology you’ve been piloting; second, educate your users; and third, turn on two-factor authentication and protect your data at scale. If we can do these three things, we can reduce the risk and be better prepared for the future.