Zero Trust Architecture
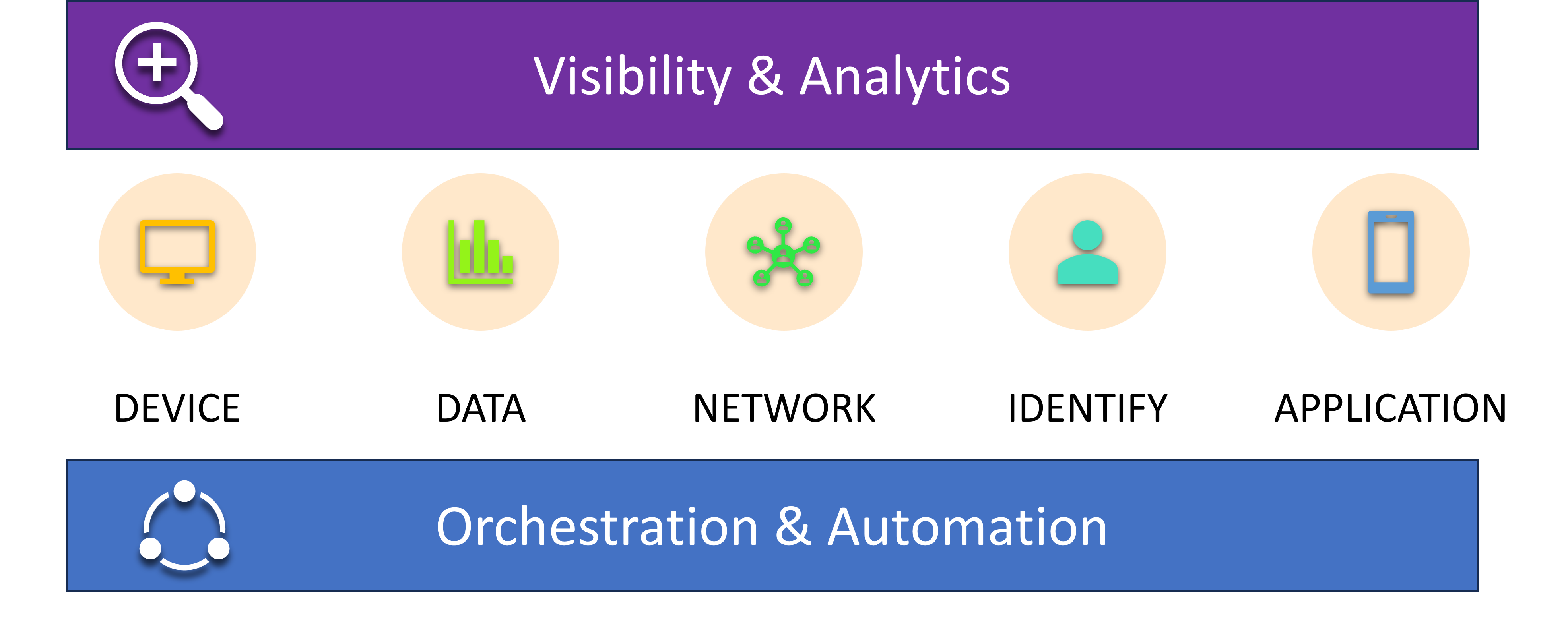
Zero trust architecture is a cybersecurity framework that assumes all network traffic, users, devices, and workloads are potentially malicious until proven otherwise. The key principles of zero trust include:
-
No implicit trust - Verify every user, device, and network flow explicitly before granting the least privileged access. Do not assume that anything already within the network perimeter is trusted.
-
• Identity-centric - Authenticate and authorize every access request by users, devices, and other entities. Strong identity systems and multi-factor authentication are essential.
-
Microsegmentation - Segment access granularly and enforce on a one-to-one level. Restrict lateral movement across networks.
-
Continuous security - Monitor and log all access and activity. Use analytics to detect threats and anomalies in real-time. Regularly reevaluate trust levels.
-
Assume breach - Adopt a mindset that breaches will occur. Use multilayered controls and security in-depth to reduce the blast radius of breaches.
The goal is to minimize access and blast radius for bad actors while providing smooth access to users with proper identity verification. Zero trust principles can apply to on-prem, cloud, and hybrid environments. Implementing zero trust requires significant resources and may impact user experience if not well-executed.
Embracing Zero Trust Series
- Zero Trust Principles - In this episode Darren explores the principles of Zero Trust architecture with special guest David Marcus, Senior Security Architect, and returning guest Dr. Anna Scott.
- Zero Trust Architecture - In this episode Darren interviews Steve Orrin and David Marcus on the key elements of Zero Trust Architecture.
- Zero Trust Applications - In this episode Darren interviews Patrick Conte from Fortanix about leveraging confidential computing in securiting applications in zero trust architectures.
- Zero Trust Operational Technology - In this episode Darren interviews the CEO of Founder of Veridify Louis Parks. They discuss the unique problems with Operational technology networks that control critical infrastructure, due to legacy complexity, accessibility vulnerabilities, and lack of visibility.
Episodes
 174 - Zero Trust Application with Confidential Computing
174 - Zero Trust Application with Confidential Computing
In this episode Darren interviews Patrick Conte from Fortanix about leveraging confidential computing in securiting applications in zero trust architectures.